Zero Trust Architecture Implementation Across Industries
by Joe Shenouda | Cyber-Consult.org
This article examines the implementation of Zero Trust Architecture (ZTA) principles across various industries, including finance, technology, energy, and healthcare. Through case studies of major corporations such as Bank of America, JPMorgan Chase, Google Cloud, Amazon Web Services, Siemens, Duke Energy, Mayo Clinic, and UnitedHealth Group, we analyze key strategies employed in ZTA implementation. These strategies include network segmentation, multi-factor authentication, continuous monitoring, and identity-based access controls.
Zero Trust Architecture Implementation Across Industries
Abstract
This article examines the implementation of Zero Trust Architecture (ZTA) principles across various industries, including finance, technology, energy, and healthcare. Through case studies of major corporations such as Bank of America, JPMorgan Chase, Google Cloud, Amazon Web Services, Siemens, Duke Energy, Mayo Clinic, and UnitedHealth Group, we analyze key strategies employed in ZTA implementation. These strategies include network segmentation, multi-factor authentication, continuous monitoring, and identity-based access controls.
1. Introduction
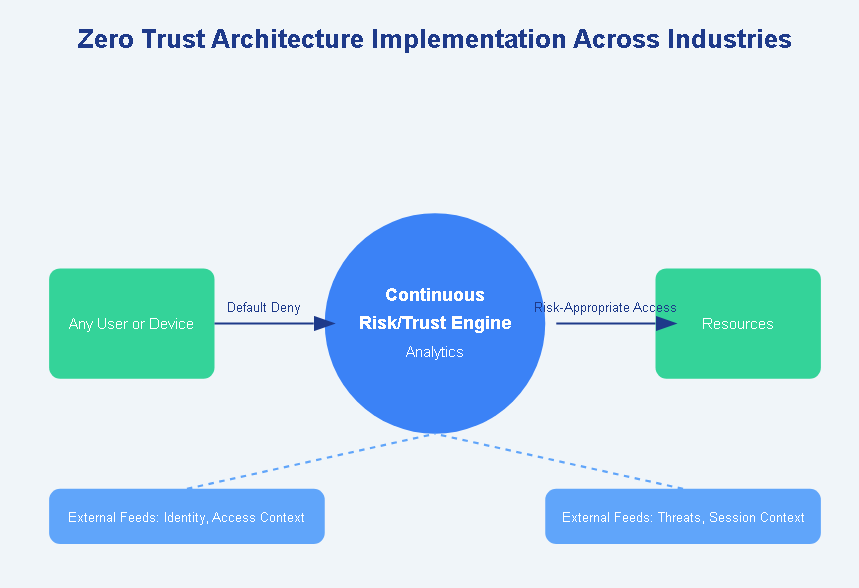
As cyber threats evolve and become more sophisticated, organizations across different sectors are adopting Zero Trust Architecture to enhance their security postures. This article explores how various industries implement ZTA principles, focusing on specific strategies and technologies employed by leading organizations.
The core tenets of Zero Trust include:
- Assuming the network is hostile.
- Assuming threats from inside and outside the network exist at all times.
- Not basing network trust on a network’s location.
- Authenticating and authorizing every requesting entity: devices, users, and networks.
- Relying on dynamic policies fed from as many sources of data as possible
2. Methodology
This article analyzes case studies from eight major organizations across four industries:
1. Finance: Bank of America, JPMorgan Chase
2. Technology: Google Cloud, Amazon Web Services (AWS)
3. Energy: Siemens, Duke Energy
4. Healthcare: Mayo Clinic, UnitedHealth Group
We examine the specific ZTA strategies implemented by each organization and their approach to addressing security challenges.
3. Results
3.1 Financial Sector
3.1.1 Bank of America
Bank of America employs the following ZTA strategies:
1. Network Segmentation: Bank of America employs microsegmentation as a critical component of its cybersecurity strategy. Microsegmentation involves dividing the network into smaller, isolated segments to limit lateral movement within the network. This approach enhances security by ensuring that even if an attacker gains access to one segment, they cannot easily move to other parts of the network. Microsegmentation allows for the implementation of granular security policies tailored to specific network segments, applications, or workloads, thereby reducing the attack surface. It also provides better visibility into network traffic, enabling the identification of abnormal patterns that might indicate a security breach. By isolating critical systems and data, Bank of America can effectively protect its assets from unauthorized access and potential data breaches.
2. Multi-Factor Authentication (MFA): To bolster security, Bank of America implements multi-factor authentication (MFA) across its systems. MFA requires users to provide multiple forms of verification before gaining access to sensitive information or systems. This typically involves something the user knows (e.g., a password), something the user has (e.g., a smartphone or hardware token), and something the user is (e.g., a fingerprint or facial recognition). By requiring multiple authentication factors, MFA significantly reduces the risk of unauthorized access, even if a user’s password is compromised. Bank of America’s use of MFA is part of a broader strategy to safeguard customer data and maintain trust in its online banking services.
3. Advanced Analytics: Bank of America leverages advanced analytics to enhance its cybersecurity posture. By employing real-time monitoring and analytics, the bank can detect anomalies and potential threats by analyzing user behavior and network traffic. Advanced analytics tools enable the bank to predict, monitor, and mitigate risks more effectively. These tools help identify unusual patterns or deviations from normal behavior, which may indicate a security threat. By integrating machine learning and artificial intelligence, Bank of America can continuously improve its threat detection capabilities and respond swiftly to emerging threats, thereby minimizing the risk of data breaches and financial losses.
3.1.2 JPMorgan Chase
JPMorgan Chase focuses on:
1. Continuous Monitoring: JPMorgan Chase utilizes continuous monitoring systems to maintain real-time visibility into its network activities. Continuous monitoring is essential for detecting and responding to security incidents promptly. By constantly observing and analyzing systems, networks, and applications, the bank can identify potential security threats, performance issues, or compliance violations as they occur. This proactive approach allows JPMorgan Chase to mitigate risks before they escalate into significant security breaches. Automated tools and processes are integral to continuous monitoring, enabling the bank to scan for vulnerabilities, detect anomalies, and generate comprehensive reports in real-time.
2. Strict Access Controls: JPMorgan Chase enforces strict access controls based on the principle of least privilege, ensuring that users have only the permissions necessary to perform their roles. This approach minimizes the risk of unauthorized access and potential data breaches. By implementing role-based access controls, the bank can manage user permissions effectively, granting access only to those who require it for their job functions. This strategy not only enhances security but also simplifies compliance with regulatory requirements. By continuously reviewing and adjusting access controls, JPMorgan Chase can adapt to changing security needs and maintain a robust security posture.
3.2 Technology Sector
3.2.1 Google Cloud
Google Cloud’s ZTA implementation includes:
1. Identity-Based Access Controls: Google Cloud integrates Zero Trust principles through identity-based access controls, which verify user identities before granting access to resources. This approach ensures that only authenticated and authorized users can access cloud services. Google Cloud’s Identity and Access Management (IAM) system allows for granular access control, enabling organizations to adopt the security principle of least privilege. By managing access at the identity level, Google Cloud can enforce strict security policies, reducing the risk of unauthorized access and data breaches. IAM also supports multi-factor authentication and federated identities, enhancing security across cloud environments.
2. Microsegmentation: Google Cloud employs microsegmentation to isolate workloads and applications, reducing the attack surface and preventing unauthorized lateral movement within the cloud environment. This technique involves creating security zones within the cloud infrastructure, each with its own set of security policies. By segmenting the network at a granular level, Google Cloud can control traffic between different segments, ensuring that only authorized communications occur. Microsegmentation provides enhanced visibility into cloud traffic, allowing for the identification of suspicious activities and quick response to potential threats. This approach is particularly effective in dynamic cloud environments where workloads frequently change.
3.2.2 Amazon Web Services (AWS)
AWS employs:
1. Transparent Shaping: AWS implements Zero Trust principles through transparent shaping, which involves shaping network traffic to enforce security policies without requiring significant code modifications. This approach allows AWS to apply security controls at the network level, ensuring that only legitimate traffic is allowed to reach applications and data. Transparent shaping helps reduce the attack surface by eliminating unnecessary pathways to sensitive resources. By continuously monitoring and adjusting network traffic, AWS can maintain a secure environment while minimizing disruptions to legitimate users. This strategy supports the seamless integration of Zero Trust principles into existing AWS workloads.
2. Security Evaluation Tools: AWS employs a variety of security evaluation tools, such as the Mozilla Observatory, to assess and enhance the security posture of applications hosted on its platform. These tools help identify vulnerabilities and misconfigurations that could be exploited by attackers. By conducting regular security assessments, AWS ensures compliance with Zero Trust principles and industry best practices. The insights gained from these evaluations enable AWS to implement targeted security improvements, reducing the risk of data breaches and enhancing overall security. AWS also provides customers with tools and resources to conduct their own security assessments, fostering a culture of shared responsibility.
3.3 Energy Sector
3.3.1 Siemens
Siemens’ ZTA approach includes:
1. Authentication and Access Control: Siemens secures its industrial control systems with robust authentication mechanisms and access control policies. These measures are designed to verify the identity of users and devices before granting access to critical systems. Siemens employs a combination of user management components and access control systems to ensure that only authorized personnel can interact with sensitive equipment. By integrating these controls into its cybersecurity framework, Siemens can protect its industrial operations from unauthorized access and potential cyber threats. This approach is critical for maintaining the integrity and reliability of industrial processes.
2. Dynamic Policy Enforcement: Siemens implements dynamic policy enforcement to adapt access controls to changing security requirements. This approach allows Siemens to respond quickly to emerging threats and evolving operational needs. By continuously monitoring security contexts and risk assessments, Siemens can adjust access policies in real-time, ensuring that only authorized entities can access sensitive resources. This flexibility is essential for maintaining a robust security posture in dynamic industrial environments. Dynamic policy enforcement also supports compliance with industry regulations and standards, reducing the risk of penalties and reputational damage.
3.3.2 Duke Energy
Duke Energy focuses on:
1. Microsegmentation and Monitoring: Duke Energy employs microsegmentation to protect its critical infrastructure, complemented by continuous threat monitoring. By isolating network segments, Duke Energy can limit lateral movement and reduce the attack surface. Continuous monitoring provides real-time visibility into network activities, enabling the detection and response to potential threats as they occur. This combination of microsegmentation and monitoring enhances the security of Duke Energy’s operations, ensuring the reliability and safety of its energy services. By leveraging advanced security technologies, Duke Energy can maintain a proactive security posture and mitigate risks effectively.
2. Dynamic Access Control: Duke Energy utilizes dynamic access control mechanisms to manage permissions based on current security contexts and risk assessments. This approach allows Duke Energy to adapt its security policies to changing operational needs and emerging threats. By continuously evaluating access requirements, Duke Energy can ensure that only authorized personnel have access to critical systems and data. Dynamic access control supports the implementation of Zero Trust principles, enhancing security and compliance with industry regulations. This strategy is essential for protecting Duke Energy’s infrastructure from unauthorized access and potential cyber threats.
3.4 Healthcare Sector
3.4.1 Mayo Clinic
Mayo Clinic’s ZTA strategies include:
1. Encryption and Data Loss Prevention: Mayo Clinic employs encryption and data loss prevention techniques to protect patient data, ensuring confidentiality and integrity. Encryption technologies, such as Secure Sockets Layer (SSL), are used to secure data during transmission, preventing unauthorized access and eavesdropping. Data loss prevention (DLP) solutions help identify and protect sensitive information from accidental or malicious data breaches. By implementing these security measures, Mayo Clinic can safeguard patient information and comply with healthcare regulations, such as HIPAA. This approach is critical for maintaining patient trust and protecting the clinic’s reputation.
2. Identity Management: Mayo Clinic uses identity management systems to authenticate users and control access to sensitive health information. These systems ensure that only authorized personnel can access patient data, reducing the risk of data breaches. By implementing role-based access controls and multi-factor authentication, Mayo Clinic can enforce strict security policies and maintain compliance with healthcare regulations. Identity management systems also support the efficient management of user identities, streamlining access provisioning and deprovisioning processes. This approach enhances the security and efficiency of Mayo Clinic’s operations.
3.4.2 UnitedHealth Group
UnitedHealth Group implements:
1. Identity and Access Management (IAM): UnitedHealth Group has implemented IAM solutions to manage user identities and enforce access controls, ensuring that only authorized personnel can access sensitive health data. IAM systems provide real-time insight into user identities, access permissions, and changes, enabling UnitedHealth Group to maintain a secure environment. By automating provisioning and deprovisioning processes, IAM solutions improve efficiency and compliance with healthcare regulations. This approach supports UnitedHealth Group’s efforts to protect patient data and maintain trust in its healthcare services.
2. Continuous Threat Detection: UnitedHealth Group employs continuous threat detection systems to monitor network activities and respond to potential security incidents in real-time. These systems provide ongoing visibility into network traffic, enabling the identification of suspicious activities and swift response to emerging threats. By leveraging advanced analytics and machine learning, UnitedHealth Group can enhance its threat detection capabilities and reduce the risk of data breaches. Continuous threat detection is a critical component of UnitedHealth Group’s cybersecurity strategy, ensuring the protection of sensitive health information and compliance with industry standards.
Conclusion
The adoption of Zero Trust Architecture principles is evident across various industries, from finance and technology to energy and healthcare. Organizations are implementing a range of strategies to enhance their cybersecurity postures, including advanced network segmentation, multi-factor authentication, continuous monitoring, and identity-based access controls. As cyber threats continue to evolve, the implementation of ZTA principles will likely become increasingly crucial for organizations seeking to protect their assets and maintain the trust of their stakeholders.
References
1. DXC Technology. (n.d.). Five steps for a Zero Trust-based approach to security in financial services. Retrieved from https://dxc.com/us/en/insights/perspectives/paper/five-steps-for-a-zero-trust-based-approach-to-security-in-financial-services
2. Security Boulevard. (2023). Applying Zero-Trust Principles: Case Studies and Lessons From the Field. Retrieved from https://securityboulevard.com/2023/06/applying-zero-trust-principles-case-studies-and-lessons-from-the-field/
3. Cloud Security Alliance. (2023). Putting Zero Trust Architecture into Financial Institutions. Retrieved from https://cloudsecurityalliance.org/blog/2023/09/27/putting-zero-trust-architecture-into-financial-institutions
4. Synpulse. (n.d.). The Evolution of Zero Trust in the Financial Sector – Strengthening Cybersecurity. Retrieved from https://www.synpulse.com/en/insights/the-evolution-of-zero-trust-in-the-financial-sector-strengthening-cybersecurity
5. Akamai. (n.d.). Zero Trust Is Revolutionizing API Security in Financial Services. Retrieved from https://www.akamai.com/blog/security/zero-trust-revolutionizing-api-security-financial-services