Navigating the Seven Seas of Vulnerability Management: A Comprehensive Guide
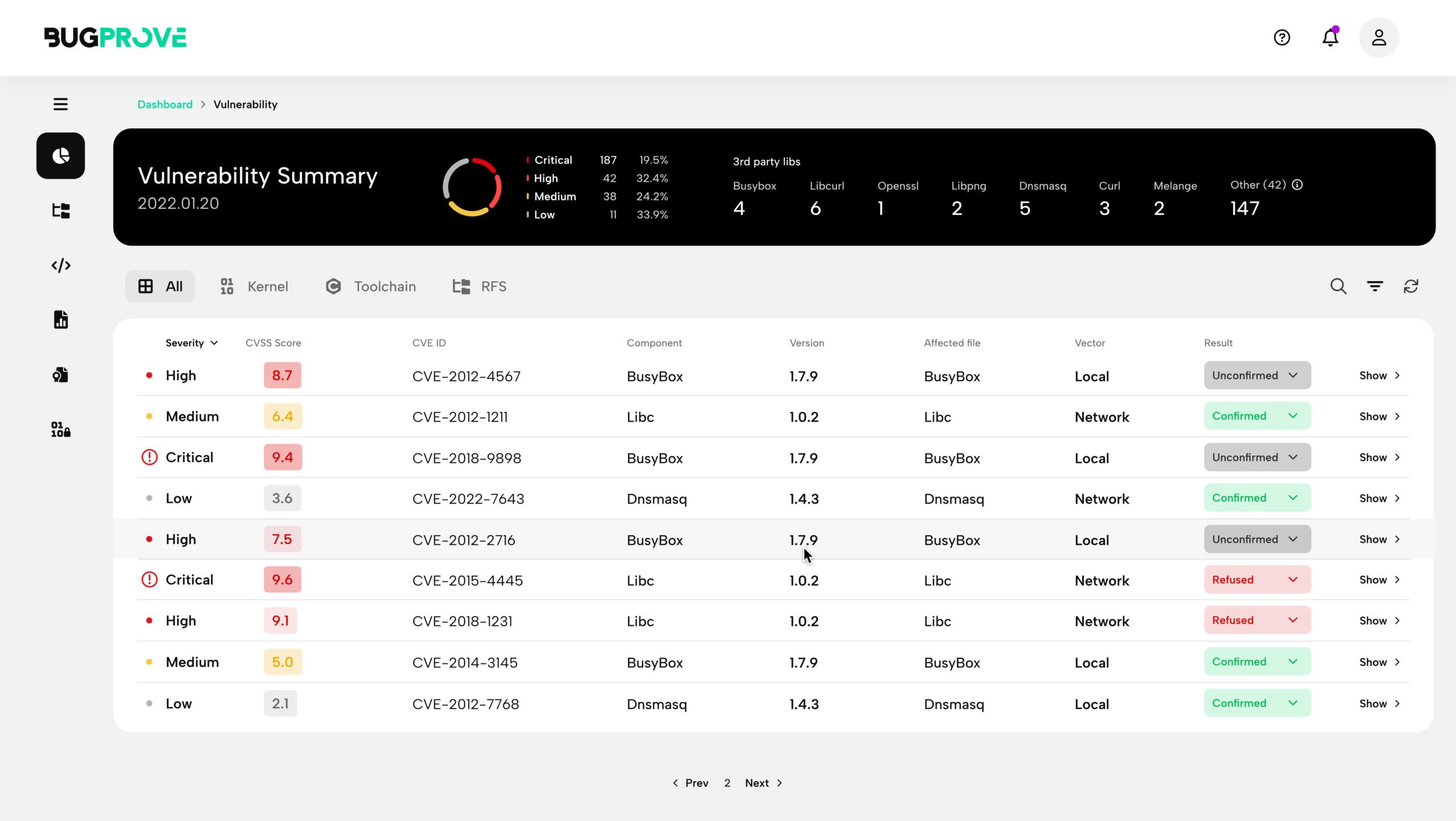
The article discusses the seven stages of the vulnerability management lifecycle. The first step is consolidation, where centralizing the cyber risk data is necessary for complete visibility, duplicate data management, and better control. The second step is correlation, where vulnerability deduplication and clustering is essential for simplified scan data management, accurate risk understanding, and improved operating efficiency. The…
Read more