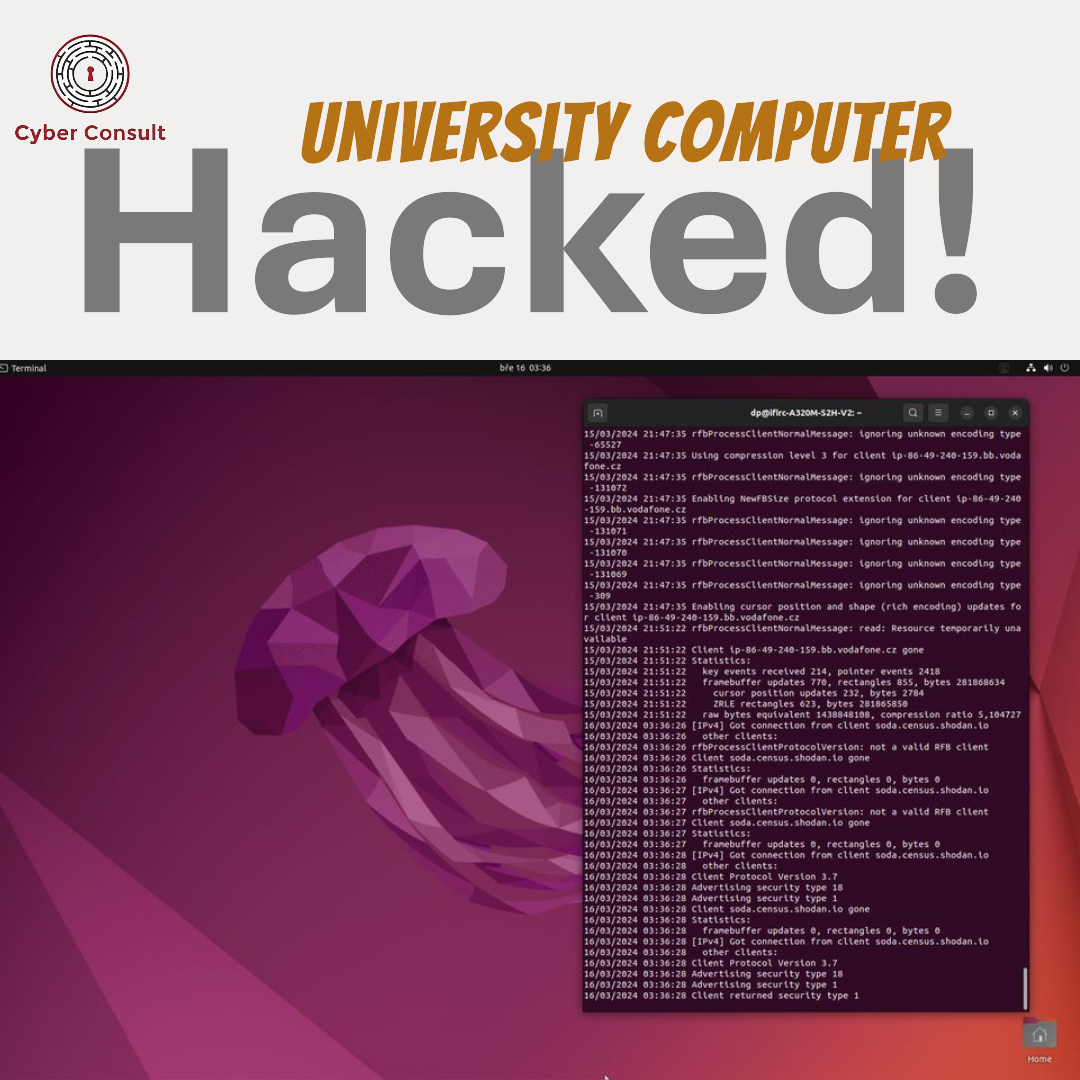
Unsecured Computer Puts Czech University at Risk
Helmond, The Netherlands – A recent cybersecurity discovery has raised alarm bells in the academic world. Security researcher Joe Shenouda from Cyber Consult uncovered a significant vulnerability in the network of Brno University of Technology, a renowned Czech institution. The finding highlights the ongoing challenges educational institutions face in safeguarding their digital infrastructure. The DiscoveryDuring a routine scan…
Read more