
If you want to share your article with us for publication, contact us


Zero Trust Architecture Implementation Across Industries
Read more
De kracht van Windows met God Mode
Read more
Unlocking the Power of Windows with God Mode
Read more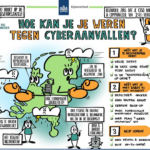
Hoe kan je je weren tegen cyberaanvallen?
Read more
Cyber-Attack Disrupts Seattle Airport
Read more
Staying Ahead of Cyber Threats
Read more
Cloud Resilience Reimagined
Read more
CodeSecDays 2024: Software Supply Chain Security Deep Dive
Read more
Navigating the AI frontier: Cybersecurity challenges and solutions
Read more
Unsecured Computer Puts Czech University at Risk
Read more
The Road to a Passwordless Future
Read more
AI NIS2 Compliance Advisor
Read more
The Human Element in Cybersecurity’s 2030 Landscape
Read more
October: Amplify Cybersecurity Awareness in Europe with NIS2 Focus
Read more
Cybergeddon: Convergence of Cyberterrorism and Cybercrime
Read more
C2000 Police Communication System Vulnerable to Hacking and Failures
Read more
Belgium’s Econocom Hacked
Read more
NIS2 Consultancy
Read more
30 Enlightening Quotes on Zero-Trust Security
Read more
Navigating the Complex Cybersecurity Salary Landscape
Read more
Transforming EU Cybersecurity: The Impact of NIS2 on Your Organisation
Read more
Environment Variables: A Security Debate at PyCon Italia 2023
Read more
RVAsec 2023 – Virginia
Read more
Tracking Mobile Phone Locations Using Silent SMS Messages
Read more
Banks Facilitating Criminal Hackers: A Growing Concern
Read more
EvilExtractor Data Theft Tool on the Rise in Europe
Read more
Limitations of Microsoft Excel in Automotive TARA Automation
Read more
How-to guide: AWS security cheat sheet
Read more
Hacker sells stolen Quran Karim Radio content to Arab countries
Read more
Modern Threat Vectors: Importance of Device-Centric Security
Read more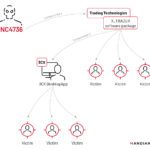
3CX VoIP Hit by Double Supply Chain Attack Targeting Crypto
Read more
Critical Vulnerability in Microsoft Outlook: How to Fix
Read more
Boost Development Lifecycle with CI/CD and Kubernetes Tools
Read more
Think Before You Share: Preventing Data Breaches in SaaS Applications
Read more
Iranian Mint Sandstorm APT Linked to US Critical Infrastructure Attacks
Read more
Joint Advisory by UK NCSC and US Agencies: APT28 Exploits Cisco Routers in 2021
Read more
IT and Security – A Love Story
Read more
DDosia: Uncovering Hacktivist Group NoName057(16)
Read more
Staying Ahead of State Hackers: The Dutch Challenge
Read more
Secure Your Business with Vulnerability Disclosure Policy Guide
Read more
9 Common GDPR Cookie Banner Blunders
Read more
Chat Services Unite Against UK Online Safety Bill: A Threat to Privacy and Security
Read more
UK police forces reprimanded for unlawful recording of 200k phone calls via app
Read more
NCR’s Aloha POS System Affected by Ransomware Attack
Read more
APT29’s Cyber Espionage Campaign on NATO and EU Countries
Read more
Access Control Benchmarks for SaaS Apps: Strengthening Your Security Posture
Read more
Securing IaC in DevOps: Best Practices and Tools
Read more
Embracing Passwordless Future with Advanced Authentication Methods
Read more
Centralized vs Decentralized Patch Management: Benefits and Comparison
Read more
9 Common CPRA Compliance Mistakes Businesses Must Avoid in California
Read more
Why WhatsApp May Consider Leaving Europe in Light of New EU Regulations
Read more
Kubernetes 1.27 Release: Enhancements and Security Updates
Read more
GitHub’s Recent Private SSH Key Exposure: Risks, Remediation, and Prevention
Read more
Hyundai Data Breach Affects Customers in Italy and France: Personal Data Compromised
Read more
Galil Sewage Recovers from Cyberattack Disrupting Irrigation
Read more
Spanish Authorities Arrest Hacker ‘Robin Hood’ for Taxpayer Data Theft
Read more
Ransomware Gangs Targeted UK: Education Sector and NHS Among the Victims
Read more
New EU Anti-Money Laundering Directive Raises Privacy Concerns
Read more
Cybersquatting Uncovered: How to Protect Your Brand and Digital Assets
Read more
Securing America’s Digital Future: Biden-Harris Cybersecurity Strategy
Read more
Information Security and Cybersecurity: Understanding the Differences
Read more
Top 8 Cloud Application Threats for European Businesses in 2023
Read more
The Vulkan Files: Leaked Documents Reveal Cyber Weapons
Read more
CryptoClippy: Malware Targets Portuguese Crypto Wallets
Read more
Beware of the Wi-Fi Queues: Researchers Find Ways to Bypass Wi-Fi Encryption
Read more
UK Honeypot Sting Exposes Thousands of Suspected Cyber Criminals
Read more
Winter Vivern Spy Gang Targets US and EU Lawmakers with Unpatched Software
Read more
Twitter’s leak illustrates why source code should never be sensitive
Read more
Cybersecurity Breach Strikes UK Criminal Records Office, Disrupting Operations
Read more
Ransomware + Healthcare: A Deadly Combination
Read more
Telegram Fraud: A Rising Concern in 2023
Read more
Genesis Market Heist: Dutch Cybercriminal Arrested for Stealing €150,000
Read more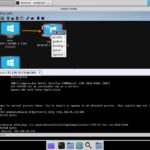
Targeted User Surveillance with WindowSpy
Read more
Securing SaaS with NIST’s Three-Pronged Approach and Contextual Data
Read more
Genesis Market Scandal: Dutch Victim Loses €70,000, 50,000 Others at Risk
Read more
Best Practices for Handling Secrets in Jenkins
Read more
Securing Communication Channels with COMSEC Tools
Read more
ChatGPT: The Star Trek Computer Come to Life
Read more
Vulnerabilities and Insights: A Look at Cybersecurity Challenges
Read more
50,000 Dutch Citizens Fall Victim to Genesis Market Cyber Attack
Read more
Boost Your GitHub and GitLab Security with Legitify’s GPT-Powered Analysis Tool
Read more
Navigating the Seven Seas of Vulnerability Management: A Comprehensive Guide
Read more
Nebu Ordered to Disclose Cyber Attack Details in Court Ruling
Read more
Free IoT Tool for Finding Zero-Day Vulnerabilities
Read more
The Art of Selling Security: How to Convince Your CFO to Invest in Your Business’s Protection
Read more
