3CX VoIP Hit by Double Supply Chain Attack Targeting Crypto
🔓 #3CX hit by a groundbreaking double #SupplyChainAttack! 😲 North Korean hackers target #Crypto businesses via a compromised employee’s PC. Stay vigilant and protect your systems! 💻🛡️ #CyberSecurity #VoIP #Malware #GopuramBackdoor
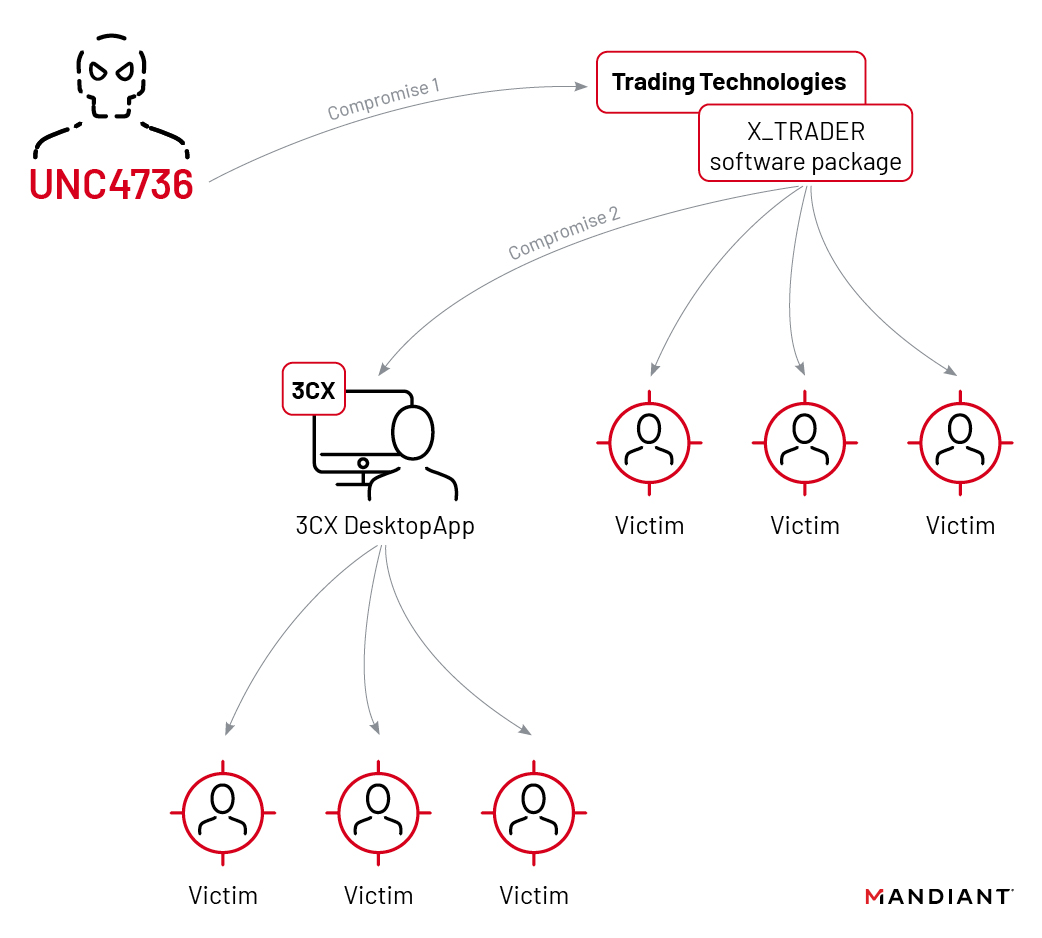
The recent supply chain attack on VoIP provider 3CX was made possible by an employee who fell victim to another supply chain attack. The employee had unknowingly installed a compromised official version of Trading Technologies’ software on their private computer. This revelation comes from a joint update provided by 3CX and cybersecurity firm Mandiant. According to Mandiant, this is the first time they have witnessed one supply chain attack leading to another.
3CX is one of the largest providers of business telephony solutions, claiming 600,000 customers and 12 million daily users. The company’s desktop application allows users to make calls and listen to voicemail from their desktops. Attackers were able to infect various versions of the software for macOS and Windows with malware.
Mandiant researchers discovered that the attackers gained access to 3CX through a compromised employee’s private computer, which had the X_Trader trading software installed from the official Trading Technologies website. The attackers had compromised Trading Technologies, allowing them to add a backdoor to X_Trader.
After compromising the 3CX employee’s private computer, the attackers stole login credentials and gained access to 3CX systems. Two days later, they were able to log in to the 3CX systems using the employee’s VPN connection. The attackers then intercepted other login credentials, moved laterally through the 3CX network, and eventually compromised the build environments for the macOS and Windows versions of the desktop application.
The malware added to the 3CX desktop application collects system and browser history information, which is sent to an attacker-controlled server. In a few select cases, the Gopuram backdoor was installed, granting the attackers access to the victim’s system. Antivirus company Kaspersky detected fewer than ten infections worldwide based on telemetry data from their clients.
According to researcher Georgy Kucherin, the primary malware and ultimate payload in the attack chain is the Gopuram backdoor, which has previously been used against crypto companies. The attackers behind the 3CX attack appear to have a specific interest in crypto businesses. Mandiant believes that a North Korea-based group is responsible for the attack.
Sources:
https://www.3cx.com/blog/news/mandiant-security-update2/
https://www.mandiant.com/resources/blog/3cx-software-supply-chain-compromise